When planning for remote access to your data hosted in the Microsoft cloud we would ideally like to say that all access must only originate from corporate devices, over which we maintain full management control. After all, we’ve gone to great lengths to secure our own hardware and have as much as confidence as possible in that kit.
App Restrictions vs App Control vs App Protection Policies, similar sounding, yet very different in impact on end users. And how do they compare against other options, Full M365 Desktop Application access and Azure Virtual Desktop. Are there other solution components we can add in?
There will always be a requirement to enable some unmanaged devices access to your data. At a very basic level this will entail ensuring that your breakglass accounts are able to access. After all, in a disaster scenario it’s possible you are not able to access corporate devices, and you need to be able to access the tenant to start restoring access to other users.
At the other end, no company is an island, we have suppliers we must receive data from and customer to who we work with. As we adopt more cloud services which facilitate collaboration, we are less likely to want to send data out on an email, knowing that data has forever left our boundary.
I will not get into the technical detail of how to implement these solutions, this post is an architectural level discussion to help guide to the correct solution based on the pros and cons of each, and hopefully avoid the practise of assigning everyone to the same solution regardless of suitability.
How to design and select the correct option
Microsoft, via their various cloud services, offer multiple different methods of enabling and securing unmanaged device access to the data in your tenant. These options are typically not single point solutions we can just deploy, rather, we can design various solutions using the following technical components. Often the connection between various settings in different admin centres is not clear.
There is not a one size fits all solution, it is essential to fully understand what the Business requirements are before we propose solutions. IT is a productivity enabler, we must be led by what the Business wishes to achieve, rather than telling what limited options we have (or worse, just providing the one option we understand).
For the purposes of this post I’ll focus primarily on access to data stored in the Microsoft 365 Productivity suite, as the tools are focused on those. That is Exchange Online and SharePoint Online/OneDrive. Some of the concepts discussed can be taken further to other data.
Technical components
What technical components are we reviewing here?
- Conditional Access
- App Restrictions
- App Control
- Intune
- App Protection Policies
- Defender for Cloud Apps
- Purview Information Protection
- Virtual Desktop
From a Marketing perspective it is entirely accurate to state that each of the above will achieve a stated goal of “Permit Unmanaged Devices to access our data”. But selecting the correct option will depend on a number of factors. What licensing is available? What solutions are already deployed? What sort of data is being accessed? What is our threat profile and risk appetite? How much overhead is required to setup and maintain this access? What costs are we willing to incur?
TL;DR – Quick comparison table
As a quick snapshot, here are the high level pros and cons of each solution. Below I will then go into more detail as to what each of these entails.
| Option | Pros | Cons |
| Full desktop application access (No restrictions) | Full M365 App functionality Simple configuration No additional licensing required | Weakest security Additional products required to secure data directly (Purview) |
| Browser – Conditional Access App Restriction | Simple configuration No impact on end user devices No additional licensing required | Support for M365/Exchange/SharePoint/OneDrive only CA policy must be targeted to these applications, requiring more policies overall Reduced M365 App functionality |
| Browser – Conditional Access App Control | Supports a wider variety of apps No impact on end user devices Provides granular control over actions within the protection application | Additional IT overhead Additional licensing – Defender for Cloud Apps Reduced M365 App functionality |
| Browser – Windows App Protection Policy | Secures all applications accessed via Edge Simple – secures all data in or out of the browser profile | Requires Intune license Requires users to create an Edge profile on their personal device Reduced M365 App functionality |
| Azure Virtual Desktop | Full M365 App functionality Full access to all LoB apps | Greatest overhead Azure costs Access granted to some internal IP networks may be security issue |
Detailed run down
We’ll now break down each of the above options in a little more detail
Full desktop applications
Allowing users to access data in Microsoft 365 via the full M365 Apps for Enterprise (Word, Outlook, Excel, PowerPoint etc) is certainly the simplest and cheapest access method.
Enabling this method simply requires that the user needing access are only targeted with a Conditional Access policy which requires Multi Factor Authentication for the grant permission (sure, we could it with out MFA, but we should not be permitting access to anyone without out at least MFA).
The main benefit to this approach is that users get the full desktop application experience. If you’ve ever tried being fully productive with the web applications you’ll know what I mean…
The main drawback however is that users will be free to save any data locally to their devices from their accounts. For low security environments, or personas who are not handling sensitive information this may be appropriate.
To mitigate this would require the deployment of Purview Sensitivity Labels. As the labels are attached to the files, protection mechanisms move with the file. Deployment of those is a entire project within itself, so unless it’s already done or actively on your radar, it’s a big undertaking to achieve the original goal of providing unmanaged device access.
Browser based solutions
If you’ve decided that full desktop application is not required, or you really don’t have the ability to deploy Purview Sensitivity labels at this time, what else can we do? The following solutions are all centred around enabling access via the users web browser. The main drawback to these solutions is that users will be working on the web based M365 apps, which can be a suboptimal experience.
Conditional Access – App Restriction
App Restrictions are a simple solution to provide an extra layer of security around the M365 online services. The restrictions are enforced by the application, meaning only applications which are built to support this will work. App Restrictions offer the following capabilities
| Location | Setting | Location |
| Microsoft 365 | Idle session timeout | M365 Admin Centre > Settings > Org Settings > Security & Privacy > Idle Session Timeout |
| SharePoint / OneDrive | Unmanaged Device Access | SharePoint Admin Centre > Policies > Unmanaged Devices |
| Exchange Online | OWA Conditional Access Policies | Configured by PowerShell using the Set-OwaMailboxPolicy command |
The main advantage of this approach is that it requires minimal extra configuration and is supported by the core M365 applications.
The drawback is the lack of configuration options available, it is a very broad everything on or off approach. If you require more granularity then you are going to need…
Conditional Access – App Control
In contrast to App Restrictions, App Control uses Defender for Cloud Apps to provide security controls within the users session, even permitting or denying specific actions.
The main advantage to this approach is the flexibility, it works with any SaaS application and any browser, and we can protect thousands of other web based applications which we can integrate via SSO with Entra as well.
The cost for this is of course greater overheads for IT and Security in the way of having a new technology to design, implement, monitor, and generally maintain. Additional licensing may be required as well.
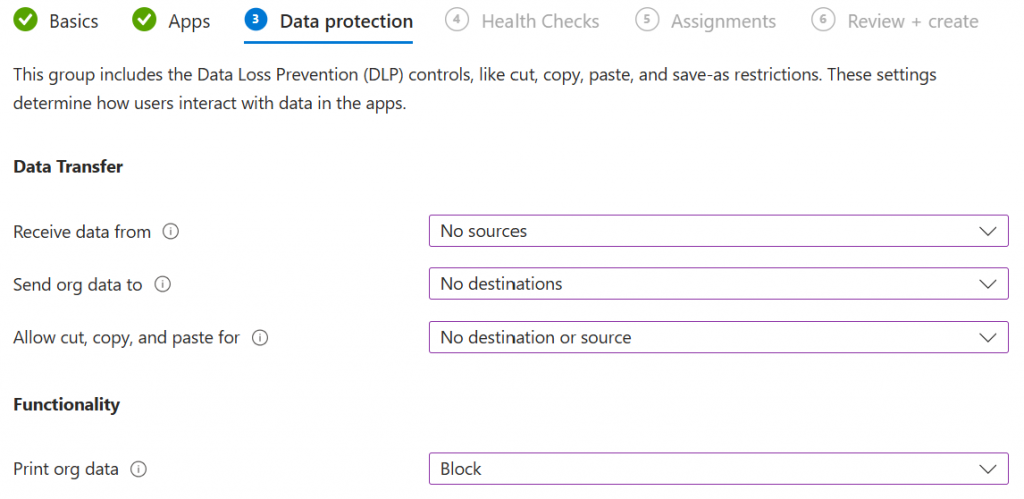
Windows App Protection – Edge
Windows App Protection policies are Mobile Application Management (MAM) policies for Windows. Currently the only application which can be used is Edge. When enabled for a user, the user creates a separate Edge profile on their personal device, which allows full control of how data can enter or leave the browser profile, providing a secure container for all web based applications.
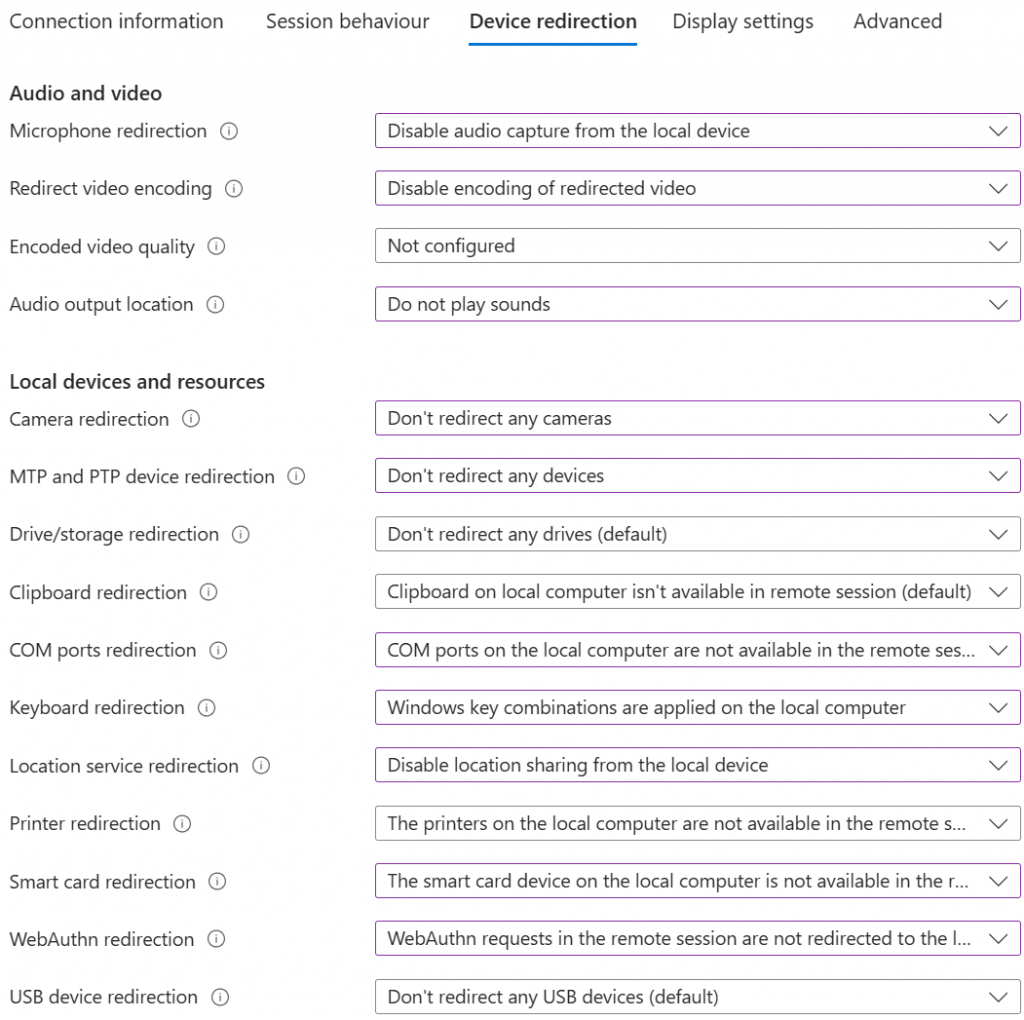
Azure Virtual Desktop
AVD arguably provides the best balance of everything, but at the highest cost – both in terms of deployment and management overheads, billable Azure costs for the VMs themselves, plus the relevant AVD license for the users.
As in the App Protection policy, it is possible to control how data can me moved in and out of the session using the Device Redirection settings. This affords us greater granularity over which devices, and therefore data, can be passed between the local device and the remote session host.
Additional considerations for AVD include; are the session hosts shared with other users/companies? Could there be data sharing issues involved? Some external users will require IP access to internal resources such as a database, but not everyone, do you need to cater for both scenarios?
Windows 365
Windows 365 sits alongside Azure Virtual Desktop, albeit the cost is likely to be higher vs a pooled session host in AVD. We have the same controls around moving data in and out of the sessions, but fewer concerns around data on the device being accessible by other users.
Conditional Access – Sign-in Frequency
The final piece in securing access from unmanaged devices is to ensure that a user is not able to log in once and then leave their device unlocked for the next 90 days, given attackers a huge windows of opportunity in their account.
What to set this level value to will depend (as always) on the data being accessed and the risk appetite of the company. From unmanaged devices it would seem sensible to set this to one day, as most people will expect to authenticate first thing when logging on. Setting it down to hourly will likely lead to MFA fatigue.
Which one is the best solution?
As with everything in IT, “it depends”. Entirely on what we want to achieve, and how we want to achieve it. With so many options available which often feel like they overlap in capability, but don’t, it can be difficult to pick one.
Start with a persona design process, the who? Who is connecting to us, to access our data. It is also worth considering where to home the user – Create a local account? Invite an external account using B2B? Entra External ID? This topic is worthy of its own blog post.
Then the where? Where are they trying to connect to? SaaS based Applications? IP based data? Is read only access required, or read/write?
Finally, how? How will they connect? The answer will be one of the solutions discussed in this article. This will lead to answering the question, what licenses do I need for this persona?
Persona Cards
Here is an example persona card I recently created for an Identity solution
| Persona Name | External Consultant |
| Comments | I am external user providing contracted services. I must correspond on behalf of JRothwell.uk and access a web based CRM secured by Entra. The data I work with must remain in the JRothwell tenant |
| Approx number in scope | 500 |
| Home tenant | Primary Jrothwell tenant |
| Licensing | F1 |
| Applications required | Exchange Online D365 – CRM |
| Device available | Personal device |
| Authentication solution | Windows App Protection policy |
| Additional comments | All services which require access are web based |
By capturing the full requirements we are able to design the best solution for a given scenario. We must resist the urge to reuse the same solutions for every remote access requirement as this can quickly lead to security being reduced as new capabilities are added to support new cases. For example, blocking copy/paste for the first tranche of users, but then permitting it for a second tranche, thus allowing the first tranche to undertake actions which they should never be able to.
Summary
Hopefully I have covered, at a very high level, the various solution options which are readily available out of the box on Microsoft cloud platforms (pending the correct licenses being available of course), and what other considerations there are to ensure as many angles as possible as covered.
Our solution options are therefore
- CA MFA + Full Desktop Applications + Sign-in Frequency + Sensitivity Labels
- CA MFA + CA App Restrictions + Sign-in Frequency
- CA App Control + Defender for Cloud + Sign-in Frequency
- App Protection Policy + Sign-in Frequency
- Azure Virtual Desktop + Sign-in Frequency
If you think I’ve overlooked anything please let me know in the comments!
